heapster가 deprecation 되면서 Metrics Server 와 통합되어 개발되고 배포되어지고 있다. 그리고 CNCF의 프로젝트중 프로메테우스도 잘 사용되어지고 있다.
# Metrics 설정
# ---------------------------------
# Metrics 설정
# ---------------------------------
# git에서 metrics-server 받아옴.
ps0107@k8smaster1:~$ git clone https://github.com/kubernetes-incubator/metrics-server.git
# metrics-server 설치
ps0107@k8smaster1:~$ kubectl create -f metrics-server/deploy/1.8+/
clusterrole.rbac.authorization.k8s.io/system:aggregated-metrics-reader created
clusterrolebinding.rbac.authorization.k8s.io/metrics-server:system:auth-delegator created
rolebinding.rbac.authorization.k8s.io/metrics-server-auth-reader created
apiservice.apiregistration.k8s.io/v1beta1.metrics.k8s.io created
serviceaccount/metrics-server created
deployment.apps/metrics-server created
service/metrics-server created
clusterrole.rbac.authorization.k8s.io/system:metrics-server created
clusterrolebinding.rbac.authorization.k8s.io/system:metrics-server created
# metrics-server pod 생성 확인
ps0107@k8smaster1:~$ kubectl -n kube-system get pods
NAME READY STATUS RESTARTS AGE
calico-node-wvxxm 2/2 Running 0 7d22h
calico-node-zxkxk 2/2 Running 2 7d22h
coredns-5c98db65d4-97gng 1/1 Running 0 7d22h
coredns-5c98db65d4-fvz2k 1/1 Running 0 7d22h
etcd-k8smaster1 1/1 Running 0 7d22h
kube-apiserver-k8smaster1 1/1 Running 0 7d22h
kube-controller-manager-k8smaster1 1/1 Running 0 7d22h
kube-proxy-t62q4 1/1 Running 0 7d22h
kube-proxy-tnmtr 1/1 Running 1 7d22h
kube-scheduler-k8smaster1 1/1 Running 0 7d22h
metrics-server-748d845495-28c7h 1/1 Running 0 15s
traefik-ingress-controller-8884w 1/1 Running 0 5h42m
traefik-ingress-controller-jdvck 1/1 Running 0 22h
# 아래 4개 라인 추가
ps0107@k8smaster1:~$ kubectl -n kube-system edit deployment metrics-server
....
command:
- /metrics-server
- --kubelet-insecure-tls
- --kubelet-preferred-address-types=InternalIP
....
deployment.extensions/metrics-server edited
ps0107@k8smaster1:~$ kubectl -n kube-system logs metrics-server-86cd7c944f-99qsx
I0205 07:28:44.958477 1 serving.go:312] Generated self-signed cert (/tmp/apiserver.crt, /tmp/apiserver.key)
I0205 07:28:46.658267 1 secure_serving.go:116] Serving securely on [::]:4443
# pod들의 metiric 정보 확인
ps0107@k8smaster1:~$ kubectl top pod --all-namespaces
NAMESPACE NAME CPU(cores) MEMORY(bytes)
kube-system calico-node-wvxxm 21m 132Mi
kube-system calico-node-zxkxk 20m 89Mi
kube-system coredns-5c98db65d4-97gng 3m 8Mi
kube-system coredns-5c98db65d4-fvz2k 3m 8Mi
kube-system etcd-k8smaster1 19m 52Mi
kube-system kube-apiserver-k8smaster1 42m 293Mi
kube-system kube-controller-manager-k8smaster1 14m 40Mi
kube-system kube-proxy-t62q4 1m 10Mi
kube-system kube-proxy-tnmtr 1m 13Mi
kube-system kube-scheduler-k8smaster1 3m 11Mi
kube-system metrics-server-86cd7c944f-99qsx 1m 11Mi
kube-system traefik-ingress-controller-8884w 4m 15Mi
kube-system traefik-ingress-controller-jdvck 4m 13Mi
# node들의 metric 정보
ps0107@k8smaster1:~$ kubectl top node
NAME CPU(cores) CPU% MEMORY(bytes) MEMORY%
k8smaster1 191m 9% 1755Mi 23%
k8sworker1 77m 3% 698Mi 9%
# api를 통해서 metric 정보를 가져올수도 있다.
ps0107@k8smaster1:~$ curl --cert ./client.pem --key ./client-key.pem --cacert ./ca.pem \
> https://10.146.0.2:6443/apis/metrics.k8s.io/v1beta1/nodes
{
"kind": "NodeMetricsList",
"apiVersion": "metrics.k8s.io/v1beta1",
"metadata": {
"selfLink": "/apis/metrics.k8s.io/v1beta1/nodes"
},
"items": [
{
"metadata": {
"name": "k8smaster1",
"selfLink": "/apis/metrics.k8s.io/v1beta1/nodes/k8smaster1",
"creationTimestamp": "2020-02-06T01:51:37Z"
},
"timestamp": "2020-02-06T01:50:42Z",
"window": "30s",
"usage": {
"cpu": "168641936n",
"memory": "1694672Ki"
}
},
{
"metadata": {
"name": "k8sworker1",
"selfLink": "/apis/metrics.k8s.io/v1beta1/nodes/k8sworker1",
"creationTimestamp": "2020-02-06T01:51:37Z"
},
"timestamp": "2020-02-06T01:50:43Z",
"window": "30s",
"usage": {
"cpu": "72926083n",
"memory": "772828Ki"
}
}
]
}# DashBoard 설정
# ---------------------------------
# DashBoard 설정
# ---------------------------------
ps0107@k8smaster1:~$ kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.0-beta4/aio/deploy/recommended.yaml
namespace/kubernetes-dashboard created
serviceaccount/kubernetes-dashboard created
service/kubernetes-dashboard created
secret/kubernetes-dashboard-certs created
secret/kubernetes-dashboard-csrf created
secret/kubernetes-dashboard-key-holder created
configmap/kubernetes-dashboard-settings created
role.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
deployment.apps/kubernetes-dashboard created
service/dashboard-metrics-scraper created
deployment.apps/dashboard-metrics-scraper created
ps0107@k8smaster1:~$ kubectl get svc --all-namespaces
NAMESPACE NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
accounting nginx-one ClusterIP 10.107.173.54 <none> 80/TCP 2d20h
accounting service-lab NodePort 10.98.40.253 <none> 80:30250/TCP 2d19h
default kubernetes ClusterIP 10.96.0.1 <none> 443/TCP 8d
default secondapp NodePort 10.107.58.46 <none> 80:31945/TCP 41h
default thirdpage NodePort 10.102.247.0 <none> 80:31715/TCP 41h
kube-system calico-typha ClusterIP 10.107.152.110 <none> 5473/TCP 8d
kube-system kube-dns ClusterIP 10.96.0.10 <none> 53/UDP,53/TCP,9153/TCP 8d
kube-system metrics-server ClusterIP 10.106.218.0 <none> 443/TCP 18h
kube-system traefik-ingress-service ClusterIP 10.109.226.41 <none> 80/TCP,8080/TCP 41h
kubernetes-dashboard dashboard-metrics-scraper ClusterIP 10.108.237.196 <none> 8000/TCP 25s
kubernetes-dashboard kubernetes-dashboard ClusterIP 10.99.196.220 <none> 443/TCP 25s
# service tyep을 NodePort로 수정해준다.
ps0107@k8smaster1:~$ kubectl -n kubernetes-dashboard edit svc kubernetes-dashboard
service/kubernetes-dashboard edited
ps0107@k8smaster1:~$ kubectl -n kubernetes-dashboard get svc kubernetes-dashboard
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kubernetes-dashboard NodePort 10.99.196.220 <none> 443:30723/TCP 2m5s
# DashBoard 접속을 위해 token정보를 얻는다.
ps0107@k8smaster1:~$ kubectl -n kubernetes-dashboard describe secrets kubernetes-dashboard-token-4p79v
Name: kubernetes-dashboard-token-4p79v
Namespace: kubernetes-dashboard
Labels: <none>
Annotations: kubernetes.io/service-account.name: kubernetes-dashboard
kubernetes.io/service-account.uid: e61f9c9a-5b45-422e-a27d-c46d935d11dc
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1025 bytes
namespace: 20 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZC10b2tlbi00cDc5diIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6ImU2MWY5YzlhLTViNDUtNDIyZS1hMjdkLWM0NmQ5MzVkMTFkYyIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlcm5ldGVzLWRhc2hib2FyZDprdWJlcm5ldGVzLWRhc2hib2FyZCJ9.UC6mVE77Kuh_gvO0mCzFE_cl9jdVHTmnSaUlzdaJroR7I6P8XCEbk8nWLmBFr7OK736QxSHNnMVIZpXbfoFi2jIoR_5MFUPomPUK-HKHRAMG84pyh-96Q_xm9SWURN8FcZTNhCq8LL5yupMic0x80F5s3l1HY1umVPDnb67EdivTVTorrDJtLuW5_F-eKIA1RA8MSPvM4KyAPZMeU5a4KPw0JFpbn4ser6I2WL-oa1xkajX2qFDasmvkkJfG9dMM_b0ALcK20Zky7bjSEy3WgkDiER5gVFr6cly6__dh0TwV2NVvmVfVl-kmWfjE5VPq7LQymQa8z3vTcQT9gBdKIQ
# ----------------------------------------------
# dashboard 로 정보가 보이지 않는 경우
# ----------------------------------------------
ps0107@k8smaster1:~$ kubectl delete clusterrolebinding kubernetes-dashboard -n kubernetes-dashboard
warning: deleting cluster-scoped resources, not scoped to the provided namespace
clusterrolebinding.rbac.authorization.k8s.io "kubernetes-dashboard" deleted
ps0107@k8smaster1:~$ kubectl create clusterrolebinding kubernetes-dashboard --clusterrole=cluster-admin --serviceaccount=kubernetes-dashboard:kubernetes-dashboard
clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
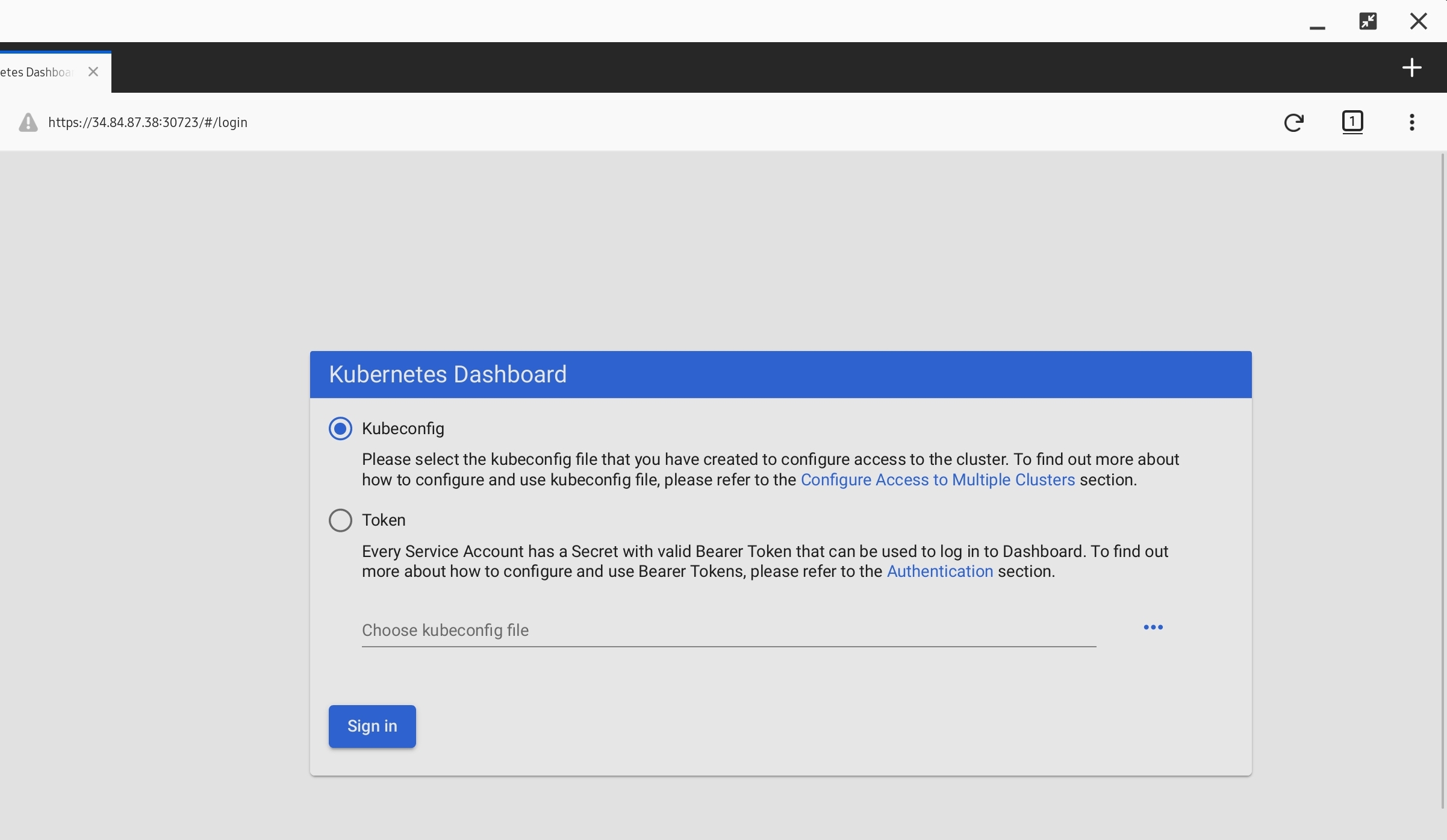
DashBoard 접속해보기
- FireFox로 접속 (https://Node_ip:NodePort)